>10,000 Windows computers may be infected by advanced NSA backdoor
Tags: your pc
>10,000 Windows computers may be infected by advanced NSA backdoor published by nherting
Writer Rating: 5.0000
Posted on 2017-04-21
Writer Description: current events
This writer has written 195 articles.
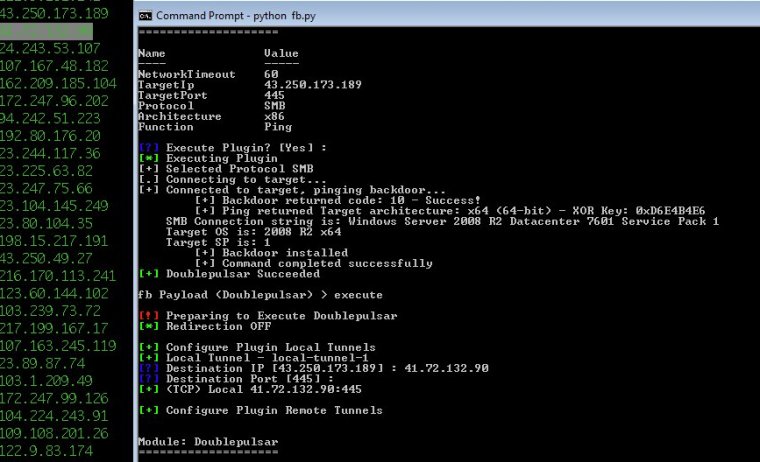
Security experts believe that tens of thousands of Windows computers may have been infected by a highly advanced National Security Agency backdoor. The NSA backdoor was included in last week's leak by the mysterious group known as Shadow Brokers.
DoublePulsar, as the NSA implant is code-named, was detected on more than 107,000 computers in one Internet scan. That scan was performed over the past few days by researchers from Binary Edge, a security firm headquartered in Switzerland. Separate mass scans, one done by Errata Security CEO Rob Graham and another by researchers from Below0day, detected roughly 41,000 and 30,000 infected machines, respectively. To remain stealthy, DoublePulsar doesn't write any files to the computers it infects. This design prevents it from persisting after an infected machine is rebooted. The lack of persistence may be one explanation for the widely differing results.
Not everyone is convinced the results are accurate. Even 30,000 infections sounds extremely high for an implant belonging to the NSA, a highly secretive agency that almost always prefers to abort a mission over risking it being detected. Critics speculate that a bug in a widely used detection script is generating false positives. Over the past 24 hours—as additional scans have continued to detect between 30,000 and 60,000 infections—a new theory has emerged: copycat hackers downloaded the DoublePulsar binary released by Shadow Brokers. The copycats then used it to infect unpatched Windows computers.
"People [who] have gotten their hands on the tools just started exploiting hosts on the Internet as fast as they could," Dan Tentler, founder of security consultant Phobos Group, told Ars. "On the part of Shadow Brokers, if their intention was to get mass infections to happen so their NSA zerodays got burned, the best [approach] is to release the tools [just before] the weekend. DoublePulsar is a means to an end."
Tentler is in the process of doing his own scan on the Shodan computer search service that makes use of the DoublePulsar detection script. So far, he has run a manual spot check on roughly 50 IP addresses that were shown to be infected. All of the manual checks detected the hosts as running the NSA backdoor. Once installed, DoublePulsar waits for certain types of data to be sent over port 445. When DoublePulsar arrives, the implant provides a distinctive response. While security practices almost always dictate the port shouldn't be exposed to the open Internet, Tentler said that advice is routinely overridden.
For the moment, readers should consider the results of these scans tentative and allow for the possibility that false positives are exaggerating the number of real-world infections. At the same time, they should be aware that there's growing consensus that from 30,000 to 107,000 Windows machines may be infected by DoublePulsar. Once hijacked, those computers may be open to other attacks.
Microsoft has yet to comment on the scan results. This post will be updated if the company responds later.
Sources: No sources found for this article.
You have the right to stay anonymous in your comments, share at your own discretion.


